
None of the information on these web pages is from any of my past work that involved security clearances. I was a member of the Association of Old Crows (AOC) for about 25 years. That was because much of the microwave electronics work I did was involved in Electronic Warfare (Wiki). I developed and oversaw the production of a combined limiter-detector that was used in the ALR series of Radar Warning Receivers that protected our aircraft from ground radar guided missiles and guns in the Vietnam era also variants in Shrike (Wiki) and HARM (Wiki) during the Vietnam era. This is described in a video tape by the AOC called "First in, Last Out". In order to gather data for our electronic warfare systems the U.S. flew over Russian radar installations. See Cold War Reconnaissance and the Shoot down Of Flight 60528. The Shrike missile used microwave detectors that were made using raw chips. This missile has the steering wings located at it's center of mass so that when it steers, it moves sideways. The AN/APR-39 was used with the ALR-xx series Radar Warning Receiver (RWR).
The Code Breakers - The Story of
Secret Writing, by David Kahn, MacMillan Publishing, First
printing 1967, mine is ninth printing 1979. Library of congress
Catalog Number 63-16109. This is a very good overview of the
history of cryptography. THE classic reference.
Surely You're Joking, Mr. Feynman!
1985, information about defeating combination locks at Los
Alamos during the Manhattan Project and many other interesting
topics.
The Puzzle Palace, by James Bamford,
Penguin Books, ISBN 0 14 00.6748 5 . First printed 1982, my copy
is 1987. This is the first book about the NSA. At the time the
book came out Washington called it "No Such Agency" but now we
know it as the "National Security Agency" the U.S. center for
codes and ciphers.
Body of Secrets is the latest book
by Bamford about the NSA. http://www.bodyofsecrets.com
is the Random House page for this book.
The Shadow Factory: The Ultra-Secret NSA
from 9/11 to the Eavesdropping on America, 2008, by
Bamford - how metadata (Wiki) from
telephone billing records was used after 9/11 to track after the
terrorists after the fact.
Also see: Spying on Cell Phones
& Orion ST616-CBS fake cell
site
No Such Agency Part Four Rigging the Game The Baltimore Sun, About December 4, 1995, pp. 9-11. Truman's 10/24/52 establishment of the NSA.
Body of Secrets : Anatomy of the Ultra-Secret National Security Agency : From the Cold War Through the Dawn of a New Century by James Bamford, Hardcover - 400 pages (April 24, 2001) Doubleday; ISBN: 0385499078 -
The Code Book by Simon Singh - Very good overview, understandable explanation of public key and the separate problem of a one way function. money challenge also descriptions of how ancient languages are decrypted even nothing is known about the language.
American Black Chamber by Herbery O. Yardley has been reprinted by Ballantine Books as part of their Espionage/Intelligence Library ISBN 0-345-29867-5
Wilderness of Mirrors
by David C. Martim, Ballantine Books as part of their
Espionage/Intelligence Library 1981, ISBN 0-345-29636-2.
Dan Rowen, US mobsters, Marilyn
Monroe, Kennedy, Bay of Pigs, Castro, aCIA
tunnel under the East-West
German border, and of course James
Jesus Angleton, Cuban missile crisis - are all covered in
this great book.
Handbook of Applied Cryptography, CRC Press (XX), ISBN: 0-8493-8523-7, October 1996, 816 pages - free chapters on line
Information and Secrecy by Colin B. Burke - 487 pages (June 1, 1994) Scarecrow Press; ISBN: 0810827832 - has some information about the U.S. Bombe made by NCR (Dayton Daily News article) to break the German Sub 4 rotor Engima
The
secret
in Building 26, Jim DeBrosse & Colin Burke, Random
House, 2004, ISBN 0-375-50807-4 - The NCR newspaper
article was expanded into this book.
The Ties That Bind by Jeffrey T. Richelson & Desmond Ball, ISBN 0-04-327092 1, first ed. 1985, Allen & Unwin Ltd. - Intelligence Cooperation between the UKSUA countries: United Kingdom, United States, Canada, Austraila and New Zealand. Chapter 8: on SIGINT with info on RHYOLITE, AN/FLR-9. Chapter 9: Ocean Surveillance has info on SOSUS, RDSS & SURTASS, Classic Wizard/White Cloud, P-3 Orion, Holystone. On pg. 225 -227 is an account of the Glomar Explorer and HMB-1 with 1985 info.
America's Secret Eyes in Space by Jeffrey T. Richlson, ISBN 0-88730-285-8 Harper & Row, 1990 The U.S. Keyhole Spy Satellite Program.
The Cuckoo's Egg by Clifford Stoll,
Doubleday, ISBN 0-385-24946-2, First Edition Oct. 1989. True
story of tracking down an international spy that was using the
internet.
Cliff's
TED talk - Klein
bottle business where I got the Chinese Spouting Bowl.-
YouTube:
The Falcon and the Snowman by Robert
Lindsey, Simon and Schuster, ISBN 0-671-24560-0 First edition
1979. The true story of how a couple of spys in the mid
1970's sold the Russians secret codes for the TSEC/KW7 that was in
a communications vault at TRW in Redondo Beach, CA. I was
working at TRW Microwave at the time and understand that a truck
load of these books were sold to TRW. 28ASR 5 level Teletype
machines used with KW-7
data encryption boxes mounted in racks.
Breaking The Ring by Johm Barron, Houghton Miffin Co. ISBN 0-395-42110-1 First edition 1987. In June of 1979 the Russians were breaking the KL-47, KL-11, KW-26, Adonis, KW7 (see Falcon & Snowman above), KY-8, KG-14, KY-36 systems "with no problems" only the KWR-37 was giving them trouble.
The Man Who Broke Purple by Ronald Clark, Little, Brown and Company, ISBN 0-316-14595-5, First American Edition, 09/77. The life of Col. William F. Friedman who deciphered the Japanese code used in WWII. Paper on Purple. Friedman coined the term "cryptanalysis" (Kahn pg 371).
The Sigint Secrets by Nigel West,
William Morrow and Company, ISBN 0-688-07652-1, First U.S.
Edition, 1988. Nigel makes a case that the Enigma was not
broken using a cryptographic attack but rather based on poor
operating practices that comprised the key setting. He says
that much can be learned about an enemy by listening to encrypted
messages without decoding the messages. This relates to
traffic analysis, i.e. who talks to who, how many messages, how
long are the messages, how strong is the signal, what bearing,
etc..
Dark Waters: An Insider's Account of the NR-1, the Cold War's Undercover Nuclear Sub, a small sub with tires it can "drive" on the botom.
Elementary Cryptanalysis a Mathematical Approach by Abraham Sinkov, The Mathimatical Association of America, LOC # 72-89953, copyright 1966 - This is an excellent book for understanding numerical methods and the application of computers. The appendix has a number of basic programs.
If you are using a computer to decrypt messages, you need a way
for the computer to know that it has succeeded. I used the
shape of the single letter frequency distribution. By
computing the square root of the sum of the squares of the
distances and normalizing the result it's easy for the computer to
solve Caesar shifts in <=26 tries.
This could be extended to general monoalphabetic cyphers by using
a diagraphic frequency distribution. For polygraphic cyphers
you would need to also look at the diagonals (both 26 up and
26 down).
Cryptonomicon by Neal Stephenson - Novel incorporating descriptions of some crypto systems and actual events. 917 pages. Counterpane Systems - Solitare - pontifex (Pearl-CGI)
AEGEAN PARK
PRESS is was a publisher of declassified
and interesting publications related to cryptography.

Cloak and Dagger
Books a very large collection of out of print books.
Decrypted Secrets: Methods and Maxims of
Cryptology by F.L. Bauer 4th ed, 2007,
ISBN13: 978-3-540-24502-5
Signal Corps Bulletin 108 Jules
Verne As A Cryptographer by Milton Friedman
War Secrets In The Ether, Part III, Wilhelm F. Flicke, NSA, 1953,
428 pages (41760949080010.pdf)
- radio related from prior to War with Poland through end of
W.W.II
Origins of SOSUS - Father of SOSUS - About IUSS -
66 Years of Undersea Surveillance, By Captain Brian Taddiken, U.S. Navy and Lieutenant Kirsten Krock, U.S. Navy, Feb 2021, Naval History, Vol 35 No. 1 -
2024 Aug 22: U.S. Naval Institute: Mysteries of the K-129, 46:46 - The purpose of the K129 mission was to verify the the key list Walker had provided actually worked. During retrofits prior to the mission the captain bribed workers to move the radio room next to the captain's berth which would be consistent with the mission.
The sea state was extremely rough. If on the surface snorkeling and there was a problem that would be catastrophic. The K129 was pretty much a copy of a German Type 21 Diesel-Electric submarine.
Once salt water gets on the battery is a catastrophe.
Based on Naval History Magazine: The Loss - and the Mysteries - of the K-129 by Capetian Jack G. Newman, U.S. Navy Reserve (Retired), 2024 Aug.
1960 K-129 Initial commissioning
1964 Captain First Rank Vladimir Ivanovich Kobzar assigned to K-129 & start of major upgrade at Dalzavod Shipyard at Vladivostok to a strategic Nuclear missile boat.
1967 Sep: John Anthony Walker (Wiki) began spying for the Soviet Union
1967 Oct-Nov: First combat duty patrol
1967 Dec to 1968 Feb in port maintenance
1968 Jan 23; USS Pueblo (AGER-2) captured by N. Korea (Wiki).
1968 Feb 9: redeploy the K-129 by the 24th
1968 Feb 13: K-129 transferred back to the crew
"Since paranoia and the irrational distrust of people bearing gifts was in keeping with the Soviet mindset, the K-129’s patrol, among other things, could have been used to verify the bona fides of John Walker’s information."
1968 Feb 24 K-129 sets sail.
re: Swordfish (Wiki) theory - "Furthermore, U.S. submarine trailing operational procedures were being established in the early 1960s. These directed that our boats, in the process of establishing a trail, should stay as far behind the Soviet submarine as possible, maintaining contact through passive sonar only." The book/movie "Hunt for Red October" gets this wrong, i.e. Crazy Ivan manovers would not cause a collusion.
"My assessment is that mechanical failure of the snorkel headvalve or system piping, plus human error, allowed seawater to enter the engine room, dooming the boat."
2024 March 31 - It turns out the crane designed and built to install the gimbals assembly into the Glomar Explorer is being used to remove the wreckage from the Key Bridge (Wiki). A crane with Cold War CIA origins will help the Baltimore bridge cleanup -
2023 April - It turns out that SOSUS made use of advanced signal processing that radically improved what can be learned from SONAR and Sonobuoys. During W.W.II the display of SONAR and Sonobuoy data was very primitive, but SOSUS and later displays were vastly improved. For more on this see SSQ-53A\Audio Analysis. This may still be classified since I have not been able to find out much about it.
2022 Feb 8: Mystery of K-129 - a Soviet Submarine Sinks during a Nuclear Launch?, 10:57 -
History's Greatest Spy Technology - Documentary - SOSUS SOSUS and the Ocean Systems Technicians MN11283 OT8 - inside of SOSUS station showing recorders
Project Caesar (LOFAR)
Report on Security of Overseas Transport. Volume 1. Project Hartwell. - see Sonobuoy Reference 4Project Caesar Shore Analysis Equipment -
Game? involving subs
1970's SOSUS History - lots of acronyms
SUBMARINES, SECRETS AND SPIES - NOVA - SOSUS helps find Scorpion (Wiki) Craven helped find it. & K-129
Cote, Owen R. Jr., “The Third Battle: Innovation in the U.S. Navy's Silent Cold War Struggle with Soviet Submarines ,” MIT Security Studies Program, March 2000
Tyler, Gordon D., Jr., “The Emergence of Low-Frequency Active Acoustics as a Critical Antisubmarine Warfare Technology,” Johns Hopkins APL Technical Digest, Vol. 13, No. 1 (1992)
Urick, Robert J., Principles
of Underwater Sound, 2nd Ed., McGraw-Hill, New York,
1975
Weir, Gary E., An Ocean in Common,
Texas A&M, College Station, 2001
Additionally, two websites have provided useful
information and general background:
1 In deep-water sound propagation, a convergence zone (CZ) is a circular ring of anomalously-low transmission loss that is caused at predictable distances from a submerged sound source by the near-surface bunching of sound rays that originally left the source over a narrow range of vertical angles. Typically, CZs appear at multiples of 30 to 35 miles from the source, but the specifics are highly dependent on the SVP and local bathymetry. Generally, much higher-than-normal target-detection probabilities are observed in the CZs.
2 By 1950, a Navy SOFAR explosion had been heard over 3,500 miles away. Moreover, several rudimentary experiments in tracking submarines with the net had shown favorable results.
3 When Ramey AFB was disestablished in 1973, the NAVFAC remained in operation but was renamed Punta Borinquen.
4 After NAVFAC Cape May was destroyed by a hurricane, it was replaced in 1962 by a new facility at Lewes, Delaware.
5 The initial first-generation SURTASS ship (Wiki) was USNS Stalwart (T-AGOS-1), commissioned in April 1984. The last of the 18 ships of that class entered service four years later.
6 John Walker, Jr. was a U.S. Navy warrant officer and career submarine communications expert who over a period of 15 years sold countless naval messages and the keys to decipher them to the Soviets, thus revealing a vast amount of highly sensitive information about U.S. naval operations and capabilities. Later, Walker recruited another Navy communications specialist, Jerry Whitworth, his brother, Arthur, and even his own son, Michael Walker, before he was turned in by his wife. All four men were arrested in 1985 and subsequently prosecuted, but by then, enormous damage to U.S. security had occurred.
7 By 1991, the existence and missions of SOSUS and IUSS had been formally declassified.
8 NOPF Dam Neck was established in 1980 as part of a major consolidation of the Western Atlantic arrays. NOPF Whidbey Island was created in 1987 to perform a similar function for the Pacific. The Joint Maritime Facility (JMF) St. Mawgan, operated in conjunction with the United Kingdom, replaced the former NAVFAC at Brawdy, Wales, in 1995.
| The K-129 (Wiki)
should have been at about 172 deg 30 min E and 40 deg
North at midnight on the night of March 7-8 (071200Z). |
'The Silent War by John Piña Craven, A Touchstone Book 2002, ISBN 0-684-87213-7 (25 years after the book "A Matter of Risk")
John wrote this book based on his own knowledge and involvement in the events described. He says that our first knowledge of the missing Russian sub was the open search by the Russians. We later discovered the SOSUS indications that the sub had gone down at 180.0 Lon x 40.0 Lat (about 2,000 miles NW of Hawaii) a point more than 300 miles off the course the Russians were searching. Doing underwater explosions as part of the research related to the Scorpion sinking led John to speculate that the explosion recorded at 180x40 had to be very loud, not something caused by an air tank imploding. Also the sub sank without the normal sounds of locked compartments imploding, meaning that the hatches were all open. This and other evidence indicated the sub was a rogue and the crew had attempted to launch a nuke missile at Hawaii, but to do this they attempted to over ride control systems that probably caused the missile to destroy itself and in the process ignited the liquid fuel carried on board the sub, causing a fire and explosion.
At that time the U.S. had the capability to do an underwater recovery to confirm the rouge nature of the sub, but instead the Glomar Explorer was constructed and deployed. One explanation for this is that the U.S. wanted the Russians to be aware that we might make make the evidence public that they had a rouge sub, and hence that they had lost control of their forces. President Nixon presented the crew of the Halibut, in Hawaii, the Presidential Unit Citation. He flew there in a secret way and not on Air Force One and there is speculation that he had some other meeting, probably with a Russian, to let them know about their rouge sub.
26 Dec 2004 - some research on the sub and what weapons it was carrying. The K-129 Diesel-electric was first called B-103 and later renamed K-129 (probably when converted to a Golf II). A 629 Golf class boat carrying liquid-propellant R-11FM with the 0.5 megaton RDS-4 nuclear explosives and/or R-13 missiles. 14 of the project 629 subs were converted to 629A Golf II class carrying the D-4 launch system and R-21 missiles with a 1400 km range. IOC was 1963.
"On 15 May 1963 deployment of the D-4 launch system on Golf and Hotel submarines began. The R-21 remained in operational service from 1963 to 1989, during which time 193 out of a total of 228 launches were successful. Over this period the service life of the fueled missile was increased from six months to two years."
The K-129 was upgraded to 629A class, see: Steel in the Deep
Note the Hawaiian islands span a distance of 1,970 to 3, 010 km from 180 Lon x 40 N Lat. (according to my globe) so if the K-129 was a Golf class then it's missile range would have been only 150 km. But a Golf II class sub carries R-21 (SS-N-5) missiles that have a range of 875 NM (1,400 km) and a payload somewhere in the 0.8 to 3.5 MT area. A 1 MT warhead has a 50% kill radius less than 20 km so it's hard to see how a Golf II sub at 180x40 could attack any of the Hawaiian islands, but is in range of Midway. 165x35 or 175x25 would get in range of Necker which is West and North of Hawaii. But in the book A Matter of Risk, the sinking subs location is given as 750 miles NW of Hawaii which would be about 165 x 30 N. Being the first book on the subject it may be wrong.
The Amazing Story of the K129 -
April 2000 Update
A couple of years ago, the Navy leased the Glomar Explorer to Global Marine, (the original contractors) for 30-years. After 20-years in mothballs, the GE was converted to a drill ship, and is currently drilling off of the coast of Nigeria. It is scheduled to return home in 3- to 4-weeks, to resume drilling in the GOM.
State-of-the-Art Drill Ship Conversion by Cascade General
Glomar Explorer (AG 193) (ex-Hugh Glomar Explorer) at the Naval Vessel Register -November 6, 2000 Russian merchant ships used in spying (this has been going on for as long as I can remember) - laser zapped eyes of 2 in helicopter. Blackbird.pdf a novel by Craig J. Coley about a similar situation.
Blind Man's Bluff : The Untold Story of American Submarine Espionage, by Sherry Sontag 1998 PublicAffairs; ISBN: 1891620088 "Most of the stories in Blind Man's Bluff have never been told publicly," they write, "and none have ever been told in this level of detail." Among their revelations is the most complete accounting to date of the 1968 disappearance of the U.S.S. Scorpion (Wiki); the story of how the Navy located a live hydrogen bomb lost by the Air Force; and a plot by the CIA and Howard Hughes to steal a Soviet sub. The most interesting chapter reveals how an American sub secretly tapped Soviet communications cables beneath the waves. Blind Man's Bluff is a compelling book about the courage, ingenuity, and patriotism of America's underwater spies.
Spy Sub by Roger C. Dunham An Onyx Book, 1997, ISBN 0-451-40797-0
This book is mostly about what it's like to serve on a sub, the Halibut, written by one of those in control if it's nuclear reactor. But it does talk about them finding and photographing the Russian sub that later was picked up by the Glomar Explorer. The photos taken by the Halibut provided much of the evidence that the sub was a rouge.
Spy Sub is the tale of a top-secret submarine named Halibut that lowered miles and miles of special cable along the bottom of the Pacific Ocean in order to investigate a sunken Soviet sub. The mission was such a success that the Halibut itself received a Presidential medal in a secret ceremony. It's a true story, even the part about the sub getting a medal. Roger C. Dunham, a nuclear reactor operator on board the Halibut during the mission, provides a firsthand account of an aspect of Cold War espionage that has only recently begun to surface. To this day, the Pentagon refuses to acknowledge such missions, in all likelihood because they are still going.
The Jennifer Project by Clyde W. Burleson, 1997 Texas A&M University Press; ISBN: 0890967644 The Jeniffer Project tells, documentary style, of the most difficult deep-sea salvage mission of all time, the CIA's effort to raise a Russian missile submarine that sank 750 miles northwest of Hawaii in 1968. Political infighting between the White House, the Pentagon, and a few select members of Congress changed a mission that was to be accomplished by small remote submarines (ala Bob Ballard/Titanic) to one which spent in excess of $200 million dollars to research, design, and built the Glomar Explorer, a one-of-a-kind salvage ship under the cover story that it was to be used by Howard Hughes to mine the world's oceans.
Other books since the original 1977 publication have shed more light on the story ("Spy Sub" & "Blind Man's Bluff" for example) of how involved the salvage mission really was. Most reports say the mission was a failure, and only part of the submarine was recovered. But one question has yet to be answered: If the submarine was to be brought up in one piece, as nearly every story written about it has stated, how then does one pull a 300+ foot long sub up through an opening of 199 feet, which was the length of the "moon pool" in the bottom of the Glomar Explorer. A very good docu-story. (ans: in three separate lifts.) Table of Contents
"S.J. Mercury, 5 Nov. 1982 dateline San Francisco- The world's first fully submersible dry dock, built as part of a CIA plan to raise a sunken Soviet sub, is being claimed by the Navy for a new secret project, it was reported Thursday. Navy officials said they have asked the National Park Service to turn over the Hughes Mining Barge-1 (HMB-1), which is docked at Todd Shipyards in San Francisco. They plan to move it to Redwood City for use in a Lockheed Missiles and Space Co. project "in which the Navy has an interest." said Lt. Commander Tom Jurkowsky, a Navy spokesman. He declined to elaborate."
A Matter of Risk by Roy Varner & Wayne Collier, Ballantine Books 1978, ISBN 0-345-28639-1 First Edition May 1980. This is the story of the Glomar Explorer built by Howard Hughes to recover the crypto equipment from a Russian Golf-class sub K-129 that sank 3 miles deep about 750 miles NW Pearl Harbor on 11 April 1968 heard by the SOSUS (see 1968) (SOSUS Museum).
Project Azorian: The Story of the Hughes Glomar Explorer
Fifty page SECRET document declassified and made public on 12 Feb 2010 at the National Security Archive web page. Jennifer was the project name for the cover story. Azorian was the overall recovery project. There was just a single lift and the sub was recovered.
Movie: Azorian: The Raising of the K-129 by Michael White
2010 - it's being shown in Europe, but not in the U.S. Maybe related to too much U.S. editing by PBS. The DVD available is only available in PAL format (not the U.S. NTSC format). I have it on order in the hopes that one of my DVD players will work on the Home Theater system. Ray Feldman worked at LMSD and on the Glomar Explorer and was an adviser on the film. He has written reviews about books on the Glomar Explorer and put me onto the author Roman Polmar and in particular "Cold War Subs".
19 Apr 2010 - the PAL DVD arrived and it plays with no problem on my Home Theater Blue-Ray player.
The movie does not address what caused the K-129 to sink or what was learned after examining the recovered front half of it. There are a lot of computer generated graphics of the Glomar Explorer and related vessels. There are also some still and movie clips that were taken at the time.
Project Jennifer was the project for generating cover stories for secret operations. Project Azorian was the project to raise the K-129. I think while the movie was being made the name Azorian was still classified and it's only in early 2010 that the name Azorian became public, hence Michael White's web page is Project Jennifer, but the released DVD is called Project Azorian.
The movie is about the Glomar Explorer and the related vessels used to raise the K-129. Early in the film there's a plot of the K-129's course which looks like a straight line, then a turn at 40 degrees North and continuing along the 40 degree latitude line until it gets to the international date line (180 degrees longitude((it doesn't matter if you call it West or East))). The explosions (there were two of them some minutes apart) happened shortly after midnight).
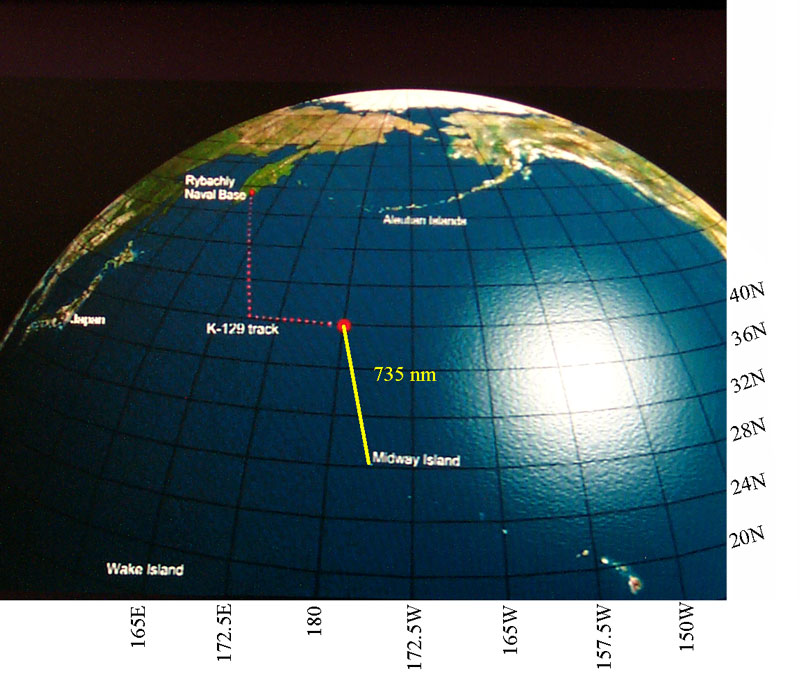 |
This map showing the path of
K-129 taken from the movie at 2:40 into the film. I have added the Lon and Lat labels and the735 nm long yellow line between the sub and Midway. It shows the path of the K-129 leaving the Naval Base on 25 Feb 1968 heading South East then making a turn at 40N, going to 180 Lon and sinking on 11 March 1968 at midnight, but the printed explosion report says 12:mm:ss and in military time that would be noon in England and midnight on the international date line. The three 1 mega ton missiles had a range of 755 nm. Note Midway is within range, but the Hawaiian Islands are not in range. |
 |
Copy of some document
relating to determining the location of the sub based on the
sound of the hull imploding. The position of these
explosions is given as: 40.1N by 179.9E at 2800 fathoms. Also note the sub was 600 nm off the path where the Russians were searching. i.e. the sub was not where it was supposed to be. |
 |
Azorian Ch2 5:12 First
Explosion time The times are when the explosion was heard at different stations. The top to bottom order of the stations is the same in both images. For example station 1 at the top heard the first explosion at 12:18:56 and the second explosion at 12:24:55. Since the explosions that were heard on the AFTAC system were caused by the hull imploding it's a good guess that something happened on the surface at exactly midnight and it took about 15 minutes for the sub to sink to a deepth where the hull would implode. |
 |
Azorian Ch2 5:21 Second
Explosion time |
AFTAC stations and the two implosions.16 Aug 2014 - Maybe if a set of equations were written with the speed of sound as a variable that was the same for all stations (really not true) and solved for the best fit an approximate location could be found that should be near 40N x 180. The Navy probably has a ray trace sound propagation software package that can be used with the approximate location and the known location of each receiving station with a more accurate propagation time for that specific path.
The speed of sound in sea water varies between 1480 (0.80 nm/sec) and 1560 m/s (0.84 nm/sec) depending on depth.
Table Distance SOUS stations to sub
Based on this table the stations should hear the explosion in the following order: 35°41′N 139°46′E
Station
Lon
Lat
Dist nm to
40N 180
Time mm:ss
@ 0 km depthTime mm:ss
@ 5.5 km depthAdak Wake Kaneohe Midway Adak
176.64 W
51.78 N
720
14:15
15:01
0
-
-
-
Wake
166.63 E
19.3 N
1420
28:06
29:37
13:51
0
-
-
Kaneohe
157.78 W
21.4 N
1591
31:29
33:11
17:14
3:23
0
-
Midway
177.35 W
28.2 N
720
14:15
15:01
0
13:51
17:14
0
Japan
139.77 E 35.7 N
1629
32:14
33:59
17:59
4:08
0:48
17:59
either Adak or Midway at the same time, then,
Wake, then
Kaneohe, then
the fifth unidentified station (most likely Japan probably because it's measured time between the first and second implosions differed from all the other stations indicating that something was wrong with it's data.)
Table: SOUS stations time of arrival. This data is not consistent with the above order of arrival. If station 2 is Adak or Midway then there should be another time for Explosion 1 very near 12:14:30 for Midway or Adak.
Station
Exp 1
Exp 2
Exp2-Exp1
Exp 1: Station# - Station 2
mm:ss
Exp 2: S#-S2
mm:ss
1
12:18:56
12:24:55
5:59
5:26
04:34
2
12:14:30
12:20:28
5:58
0
0
3
12:33:22
12:39:20
5:58
18:52
15:54
4
12:30:12
12:36:10
5:58
15:41
13:13
5
12:40:30
12:47:13
6:17
27:00
22:45
The CIA's Greatest Covert Operatioon: Inside the Daring Mission to REcover a Nuclear-Armed Soviet Sub, David H. Sharp, 2012, Remaining Mysteries:
2024 August: U.S. Naval Institute: The Loss—and the Mysteries—of the K-129: The disappearance of a Soviet submarine in the Pacific—and the CIA’s clandestine effort to retrieve the wreck—remains one of the most intriguing chapters in the story of the Cold War. Here is an inside account from a former submarine officer who was there. - posits a battery explosion
- The actual intelligence that was gleaned from the sub
- What the intelligence community knows about the cause of the K-129 loss
- What would have happened if the Glomar Explorer was capture
2025 Update
Watched the movie The Real Hunt for Red October (IMDB), 2021 - Tries to make the case that the book was sponsored by the CIA and related to the K129.
The movie and Wiki K129 web page say "The purpose of that secrecy, he alleged, is to stop any further research into the losses of USS Scorpion and K-129. Huchthausen reported that Dygalo told him to "overlook this matter, and hope that the time will come when the truth will be told to the families of the victims." The implication was that Russia sank the scorpion in retalliation for the US sinking the K129.
The movie says the location was found because of a radioactive oil slick and does not get into the SOSUS/AFTAC data that way they can claim the prior locations were also cover stories and the sub was much closer to the Hawaiian islands. There were a number of places where there appeared to be errors, but they did make a case that the CIA may have been a source for the book and helped promote it. The book was published by the Naval Institute Press, quite a feat for an unknown author!
The following book was used in the above movie as a referencer.
The Taking of K-129: How the CIA Used Howard Hughes to Steal a Russian Sub in the Most Daring Covert Operation in History, 2018, Josh Dean - 2025 March just starting to read.
There is no Table of Contents. There is a bibliography (Archive.org - with links) and index, Sources. The book's web page has now expired.
Acoustic Detections of the Loss of the GOLF II Class Soviet SSB K-129 - "Analysis of the AFTAC acoustic data obtained from public domain sources in 2008 established—for the first time—that the K-129 was lost because three explosions occurred within the pressure hull immediately prior to an apparent dual R-21/D4 missile launch training event scheduled for 12:00:00Z on 11 March 1968, hereafter referred to as T-0. Those explosions allowed that training event to become the firing to fuel exhaustion of two R-21/D4 missile (Wiki) within their closed—but subsequently breached—launch tubes. The AFTAC data confirms these R-21/D4 firing events and launch support system activity occurred over an eight minutes and 36 second period following ignition of the first missile. That launch support activity, apparently directed by a programmed launch sequence control system, remained at least partially operational despite the almost certain death of the crew from the first internal explosive that occurred 62 seconds before ignition of the first missile (T-62 seconds)." The first missile fired at exactly midnight, but was locked into the launch tube and so burned through the tube and burned up the sub.
Acoustics Has the Last Word (for Some) on the Loss of the Soviet Submarine K-129 on 11 Mar 68 - "On the subjective side, there are others reasons for dismissing involvement by SWORDFISH – or any other US platform - with the K-129. First, as pointed out by someone else, how likely is it that none of the 130 or so members of the SWORDFISH crew would have remained silent for 45 years had their ship sunk the K-129, and, be assured, the long range acoustic data indicates any platform in the immediate vicinity equipped with a passive sonar would have known the K-129 had sunk." "Second and, I think, even more compelling, is the consideration that had a fatal (for the K-129) collision with a US submarine actually occurred, the last thing the US would have wanted to do would have been to attempt to recover the wreck and possibly expose evidence of a collision to the hundreds of personnel aboard the CIA salvage ship who would see that evidence: the exchange principle (Wiki). (1) It would appear that imagery available on the K-129 before the salvage attempt was not of high enough quality or of sufficient coverage to establish no such evidence would be apparent upon close inspection of the wreck."
YouTube: Пропавшая субмарина. Трагедия К-129, 43:58 - CC+On, Auto-Translate=English; 5 Jan 1968, two months prior to the K129 sinking, The Pueblo Incident (Wiki) puts the Russians are on high alert. - @about 12:00 they implicate the Sordfish;
The SOSUS system originally only listened to low frequency sounds, like from submarine propellers. Later it was modified to also listen for Earth tremors related to detect atomic bomb testing (Wiki). Still later it was modified to detect the splash down of Russian missile nose cones so they could be retrieved (Wiki).
CIA Reading Room: Project Azorian: The Story of the Hughes Glomar Explorer, 50 pages - many redactions -
NPS: Fixed Sonar Systems; The History and Future of the Underwater Silent Sentinel, LT John Howard, USN, April 20112, 12 pages -
K129 sank on 1968 March 8.
2025 June 22: YouTube: Incredible Stories: Soviet's K-129 Mystery Finally Solved in 2025, And It Was Worse Than We Thought, 25:40 - claim that missile was fired and splashed down in the Pacific and may have been recovered. But no evidence or references given, so total speculation.
3215976 Method for surveying and searching the ocean bottom and recovering objects therefrom, Willard N Bascom, Ocean Science and Engineering, 1965-11-02, - intended for treasure hunting, but may have found an application in the Missile Impact Location System (Wiki: MILS) -
3336003 Travelling block guide, Crooke Robert Curtis, Mar Corona Del, Knorr Gordon Dayton, Global Marine, 1967-08-15, -
3458853 Underwater guidance method and apparatus, Charles K Daniels, John P Mccarthy, EG&G, App: 1967-08-08, Pub: 1969-07-29, - before K129 sank, so patent 3731263 probably not related to K129
3469820 Drill pipe stabilizing apparatus, Edward E Horton, Ocean Science and Engineering, 1969-09-30, - heave compensation
3481299 Control apparatus, Kurt Horn, Honeywell, 1969-12-02, - propellers are in a fixed position
3548775 Control apparatus, Clarence H Hammond, Kurt Horn, Honeywell, 1970-12-22, - Four thrusters, similar to outboard motors, used for station keeping, adjustable azimuth and power (10 to 90%).
3549129 Motion dampening device, John R Graham, Rene M Delaunay, Global Marine, 1970-12-22, - /works with a towing cable, not pipe
3731263 Underwater guidance method and apparatus, C Daniels, J Mccarthy, EG&G, App: 1971-04-28, Pub: 1973-05-01, -
3622962 Free fall oceanographic beacon, Clifford L Winget, Thomas B Aldrich, Navy, App: 1969-09-09, Pub: 1971-11-23, - would be a handy way to mark the location - "... it will be seen that the assembled apparatus has as its buoyant member a cylindrical float 1, made preferably of syntactic foam. This material, as is well known, consists of microsphere hollow glass beads embedded in a resin material or binder. This composition has a density less than that of sea water, and its compressive strength is such that it will not collapse at the high-static pressures encountered in the deepest ocean environment."
3860900 Method of monitoring the position of towed underwater apparatus, Ronald J Scudder, Western Electric, 1975-01-14, - "Examples of such operations include the installation of underwater pertroleum equipment, exploration for sea floor minerals, and the laying of cables and pipelines."
3894640 Apparatus for raising and lowering large objects from a surface ship, R Curtis Crooke, John R Graham, James F Mcnary, Global Marine, 1975-07-15, - Glomar Explorer
3916810 Stabilizing means for air or water borne vehicles, Charlie L Johnson, 1975-11-04, -
3918379 Gimbal support system for deep ocean mining vessel, James F Mcnary, Edward C Hicks, Yilmaz H Ozudogru, Global Marine, 1975-11-11, - Glomar Explorer
3943868 Heave compensation apparatus for a marine mining vessel, Abraham Person, Vance E. Bolding, Global Marine, 1976-03-16, - Glomar Explorer
3949883 Hydraulically operated heavy lift system for vertically moving a string of pipe, Robert C. Crooke, Abraham Person, Global Marine, 1976-04-13, - Glomar Explorer
4039177 Heave compensation apparatus for a marine mining vessel, Abraham Person, Vance E. Bolding, Global Marine, 1977-08-02, - Glomar Explorer
4070671 Navigation reference system, James A. Morrow, Rockwell International Corp, 1978-01-24, -
4165706 Submersible vehicle deployment and recovery system for rough water, John S. Parsons, Global Marine, 1979-08-28, -
4176722 Marine riser system with dual purpose lift and heave compensator mechanism, Sherman B. Wetmore, James F. McNary, Abraham Person, Deepsea Ventures (Global Marine), 1979-12-04, -
The CIA's Greatest Covert Operation: Inside the Daring Mission to Recover a Nuclear-Armed Soviet Sub, David H. Sharp, 2012, 344 pages -
The Glomar (GLObal MARine) Challenger (Wiki) was a precursor to the Glomar Explorer as was Project Mohole (Wiki) where dynamic positioning (Wiki) was developed.
YouTube: 60 Minutes: Submarines (from 1998) 1:13:25 - K-129; Halibut (SSGN-587) (Wiki);
0:00 Intro
0:11 The Silent Service (1998)
13:32 Trident, Do We Need It? (1973)
30:06 The New Cold War (2016)
42:56 The High North (2019)
55:59 The Arctic Frontier (2016)
1:10:28 Andy Rooney Goes On a Nuclear Submarine (1999)
The U.S. handling of the secret messages has been thoroughly investigated with the conclusion that there were a number of mistakes. My own theory is based on the fact that England had a well oiled system of intercepting, decrypting, and disseminating the fruit of the intercepted messages. The method of communication at the time was H.F. radio that not only goes to the recipient but also "skips" all over the world. I think that England received the same messages that the U.S. did, but unlike us, both decoded them and understood what they meant. I believe that England communicated to the U.S. that Pearl Harbor would be attacked and about when.In Jan. 1941 Abe Sinkov, Leo Rosen, Robert Weeks and Prescott Currier hand delivered to B.P. a working Purple machine, a kana typewriter, and stacks of documents. Starting Feb. 1941 SIS and OP-20-G the Purple messages were read almost currently. (from a book about Purple.) This may not be too important if JN25 was used for pre-attack messages, or they may have gleaned some info from Purple.
Trivia: To prevent robbers forcing jewelers or bank managers to open their vaults at gun point it was common to use time locks set to only allow opening during business hours Monday through Friday. Time locks were used at Pearl Harbor and since the attack happened on a Sunday, they could no open their safes. This drove development of better combination locks.
1 Meter Resolution
These companies started offering in 1999 high resolution 1 meter photographs made to order.
Prior to this the resolution was 5 meters or greater.Autometric - incorporated in Cayman Islands
Earth Watch Inc. - Quickbird 1 -
Space Imaging, Inc. - Ikonos -
Orbital Imaging Corp. - OrbView-3 and OrbView-4 - in full minute increments with a minimum requirement of a continuous two-minute imaging window. The pricing is $10,000 per minute
FAS - Imint Gallery -
Global Security - Picture of the Week (click on image for new web page)
5 Meter & Greater Resolution
SPOT - French - 5 - 10 meter
Terra Server - my locationN39:11:24.692 - W123:09:50.548 -
USGS - National Mapping and Remotely Sensed Data - Earth Resources Observation System (EROS Data Center) - Multispectral Scanner Landsat Data - 50 meter
Earth Observing System Data Gateway -? Resolution
GlobeXplorer - works like Terra Server
Advanced
Encryption Standard (AES) - on the NIST Encryption web page
that also has some declassified information on KEA and Skipjack
Association of Old Crows - for
people involved in Electronic Warefare
Cryptographic Module
Validation (CMV) Program -
Air Force Technical Applications
Center - McClellan
Air Force Base - responsibility for managing the
Atomic Energy Detection System [AEDS] discovering foreign atomic
tests and other nuclear weapons related activities
Alan Turing Home Page
by the author of a book about the man who thought of the "Turing
Machine" and developed code breaking computers in England
alt.locksmithing answers to Frequently
Asked Questions (FAQ)

Alphabetical List, Brooke's Home, Crypto Machines, Military Information, Electronics, Page
Page created: 30 Jan. 2000.